FakeKitten 2, upload anything on amazon photos, now with encryption
this was the happy cat we were using as deceit image in the previous version,
now it looks like this:
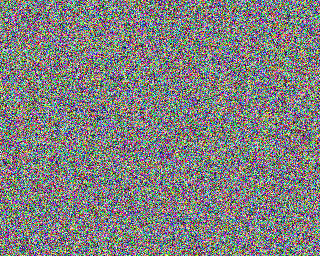
the updates:
- [x] now uses random images
- [x] filename is of a raw file (.DNG) so Amazon Photos does not try to fiddle with the image
- [x] added encryption
- [x] checks for prerequisites (convert and gpg)
you can find the old article here: FakeKitten, or how to trick Amazon Prime Photos to store anything
let's see what changed:
a simple script to upload whatever on Amazon Prime Photos
¯\(ツ)/¯
why: #
Amazon Prime Photos allows you to upload everything as long as it's an image,
giving you unlimited storage (I expect them to do facial recognitioning or other unholy things with your images).
so we can leverage this dynamic to upload any file to resemble an image,
just by appending the original file at the end of a random image we are generating on the fly.
the images will be saved as a raw image file, .DNG extension, so the site won't touch it trying to re-compress the image to save files
I've tried to upload files and managed to get 3.5GB without issues
usage: #
encoding: #
./FakeKitten.sh yourfile.pdf encode
you will obtain a file named:
FakeKitten_143442_yourfile.pdf_3a1863591abdce897987971928512865db_random.DNG
where the file name is composed like this:
[constant]\_[image blocksize]\_[originale filename]\_[sha1sum of the original file]\_[decoy image filename]
at this point you can manually upload it on Amazon Prime Photos
encoding and encrypt your file: #
use encode_enc:
./FakeKitten.sh yourfile.pdf encode_enc
this will use a symmetric password for the encryption with gpg,
you will be asked for said password with a prompt
the different thing with the normal encoding is the filename, which will be:
FakeKittenENC_143442_yourfile.pdf**.gpg**_3a1863591abdce897987971928512865db_random.DNG
decoding: #
decoding will automatically take care of differentiating between an encrypted and non-encrypted original file,
if the file was encrypted you will be asked for the password
./FakeKitten.sh FakeKitten_143442_yourfile.pdf_3a1863591abdce897987971928512865db_random.DNG decode
you will obtain your original file:
yourfile.pdf
The new script: #
#!/usr/bin/env bash
if [ -z "$1" ] || [ -z "$2" ] || [[ $2 != "encode" && $2 != "decode" && $2 != "encode_enc" ]]
then echo "launch the script with the desired filename and operation"
echo "./AmazonPrimeWhatever.sh FILENAME OPERATION(encode or decode)"
exit
fi
# check for prerequisites:
if ! [ -x "$(command -v convert)" ]; then
echo 'Error: convert (part of the imagemagick suite) is not installed.' >&2
exit 1
fi
if [ $2 = "encode_enc" ] || [ $(echo $1 | cut -d "_" -f1) = "FakeKittenENC" ]; then
if ! [ -x "$(command -v gpg)" ]; then
echo 'Error: gpg is not installed, it is needed for encryption/decryption' >&2
exit 1
fi
fi
if [ $2 = "encode" ] || [ $2 = "encode_enc" ]; then
imagejpg="random.jpg"
image="random.DNG"
#generate random image:
mx=320;my=256;head -c "$((3*mx*my))" /dev/urandom | convert -depth 8 -size "${mx}x${my}" RGB:- $imagejpg
mv $imagejpg $image
imagesize=$(du -b $image | cut -f1)
if [ $2 = "encode" ]; then
origsha=$(sha1sum $1 | cut -d " " -f1)
destimage="FakeKitten_"$imagesize"_"$1"_"$origsha"_"$image
mv $image $destimage
dd if=$1 bs=1M >> "$destimage"
echo "encode completed in $destimage"
fi
if [ $2 = "encode_enc" ]; then
#
gpg --symmetric --cipher-algo AES256 $1
#
origsha=$(sha1sum $1.gpg | cut -d " " -f1)
destimage="FakeKittenENC_"$imagesize"_"$1.gpg"_"$origsha"_"$image
mv $image $destimage
dd if=$1.gpg bs=1M >> "$destimage"
echo "encode completed in $destimage"
fi
fi
if [ $2 = "decode" ]; then
imageconst=$(echo $1 | cut -d "_" -f1)
imagebs=$(echo $1 | cut -d "_" -f2)
origname=$(echo $1 | cut -d "_" -f3)
origsha=$(echo $1 | cut -d "_" -f4)
origimage=$(echo $1 | cut -d "_" -f5)
dd if=$1 bs=1M skip=$imagebs iflag=skip_bytes > "$origname"
if [ $imageconst = "FakeKittenENC" ]; then
#decrypt the file
orignamenogpg=$(echo "$origname" | sed 's/.gpg//')
gpg --output $orignamenogpg --decrypt $origname
fi
echo "decode completed in $origname, checking file integrity"
echo $origsha" "$origname > $origname".sha1"
shaoutput=$(sha1sum -c $origname".sha1")
echo $shaoutput
if [[ $shaoutput != *"OK"* ]]; then
echo ""
echo "!!! FAILED SHA VERIFICATION!!! EXITING"
echo "!!! DELETING ALL CREATED FILES !!!"
rm $origname
rm $origname".sha1"
exit
fi
if [ $imageconst = "FakeKittenENC" ]; then
#remove the file that contains .gpg at the end
rm $origname
fi
rm $origname".sha1"
fi
echo ""
echo "end of my job"